100% Pass Cisco, PMP, CISA, CISM, AWS Dumps on SALE!
Get Now
01:59:56
X
Cisco Club

What are the advantages of intrusion prevention technology?
2020-08-30
With the continuous improvement of network attack technology and the continuous discovery of network security vulnerabilities, traditional firewall technology plus traditional IDS technology can no longer cope with some security threats.

Five advantages of NETCONF protocol
2020-08-29
With the upsurge of SDN over the years, a ten-year-old protocol has once again attracted people's attention, and it is the NETCONF protocol.
The network configuration protocol NETCONF (Network Configuration Protocol) provides a mechanism for managing network devices. Users can use this mechanism to add, modify, and delete the configuration of network devices, and obtain configuration and status information of network devices.

Detailed VRRP technology
2020-08-24
In the VRRP standard protocol mode, only the Master router can forward packets, and the Backup router is in the listening state and cannot forward packets.
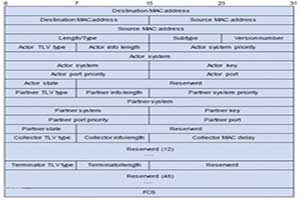
LACP technology explained
2020-08-18
In short, Link Aggregation technology is to aggregate multiple physical links into a logical link with a higher bandwidth.

What is WLAN WDS technology
2020-08-17
Wireless Distribution System means that APs connect two or more independent local area networks through wireless links to form an interconnected network for data transmission.

Three advantages of MSDP protocol
2020-08-13
MSDP, short for Multicast Source Discovery Protocol (Multicast Source Discovery Protocol), is an inter-domain multicast solution developed to solve the interconnection between multiple PIM-SM (Protocol Independent Multicast Sparse Mode) domains. Program.

Quickly understand terminal access technology
2020-08-12
Terminal access means that the terminal device is connected to the router, and the data communication between the terminal device and other terminal devices is completed through the router.

How to effectively prevent VLAN attacks?
2020-08-11
VLAN (VirtualLocal Area Network). VLAN is a group of logical devices and users. These devices and users are not restricted by their physical location.
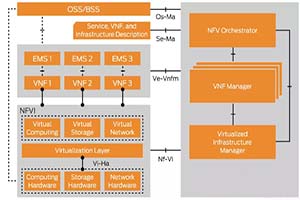
Master the basic concepts of NFV in 1 minute
2020-08-10
The standard architecture of NFV includes three parts: NFVI, MANO and VNFs. The goal of Network Function Virtualization (NFV) technology is to provide network functions on standard servers, rather than on custom devices.
Cisco Dumps Popular Search:
ccna 100-105 pdf 350-801 clcor book pdf ccna 200-301 book pdf download ccnp route cheat sheet pdf ccie lab hardware list how to master ccnp tshoot pdf 350-401 vceplus 200-301 amazon ccie security syllabus ine ccie lab
Copyright © 2026 PASSHOT All rights reserved.






