100% Pass Cisco, PMP, CISA, CISM, AWS Dumps on SALE!
Get Now
01:59:56
X
Understand the new security protection mechanism AppDefense
Traditional application security protection mechanisms are passive. To detect malicious attacks on applications in time, you must first understand the characteristics of the attack methods. For example, antivirus software has a "virus signature database" that uses signature codes to scan and Virus code found.
The biggest problem with this method is that it cannot prevent unknown means of attack, and the protection mechanism is lagging. In recent years, with the development of artificial intelligence technology, machine learning has also been applied to detect unknown attack methods. Through the collection and analysis of data in the computing environment, we can find out unusual behaviors, which may be potential Aggressive behavior.
The challenge of this method lies in how to deal with the massive amount of environmental noise and how to filter out the results we want from the noise, which often causes misjudgments in practical applications.
VMware's innovative product AppDefense has created a new way of creating a new security protection mechanism, which is embedded in the vSphere Hypervisor to achieve comprehensive security protection for virtual machines. The innovation of AppDefense is mainly reflected in the following three aspects:
Active security protection: detect "bad" attacks by understanding the "good" state of the virtual machine, instead of passively responding to malicious attacks like traditional security mechanisms, but actively defining the state that the system should have in normal operation , When a deviation from normal behavior is detected, it may be a malicious attack.
Because AppDefense exists in the virtualization layer, it has a unique advantage to understand the normal behavior of each virtual machine or application, and can also know any changes in the virtual machine at the first time. This advantage greatly improves the intelligence of AppDefense, eliminating the need to guess which changes are normal and which behaviors are potential threats.
AppDefense does not monitor a specific virtual machine in isolation, but considers security from the perspective of the entire data center. This allows AppDefense to understand the complex interactive behavior patterns between virtual machines.
Automatic and accurate threat response: Automatically respond to security threats at the right point in time. Whenever a malicious attack is detected, AppDefense can automatically call the functions of vSphere and NSX to automatically take security measures:
• Block process communication
• Grab a snapshot of the virtual machine for further analysis
• Suspend the infected virtual machine
• Turn off the infected virtual machine
Isolate from the attack surface: Most malware attacks the security protection system first, such as banning antivirus software, or paralyzing security protection agents, to create conditions for further attacks.
AppDefense exists in the Hypervisor. This location keeps it away from the attack surface and has natural security, which is unmatched by any security software running on a virtual machine.
Let's take a look at the system architecture of AppDefense. AppDefense is a service provided in the form of cloud SaaS. After users log in to the AppDefense Manager in the cloud, they can download the following three modules:
• AppDefense Appliance: The user needs to deploy such a virtual machine in the data center to be responsible for
AppDefense has all management functions and is responsible for communication with the cloud AppDefense Manager.
• Host Module: Provided in the form of VIB (VMware Installable Bundles) and installed in the ESXi Hypervisor of each physical server.
• Guest Module: is an executable installation package that is installed on each virtual machine. The Guest Module and Host Module work together to monitor the behavior of the virtual machine.
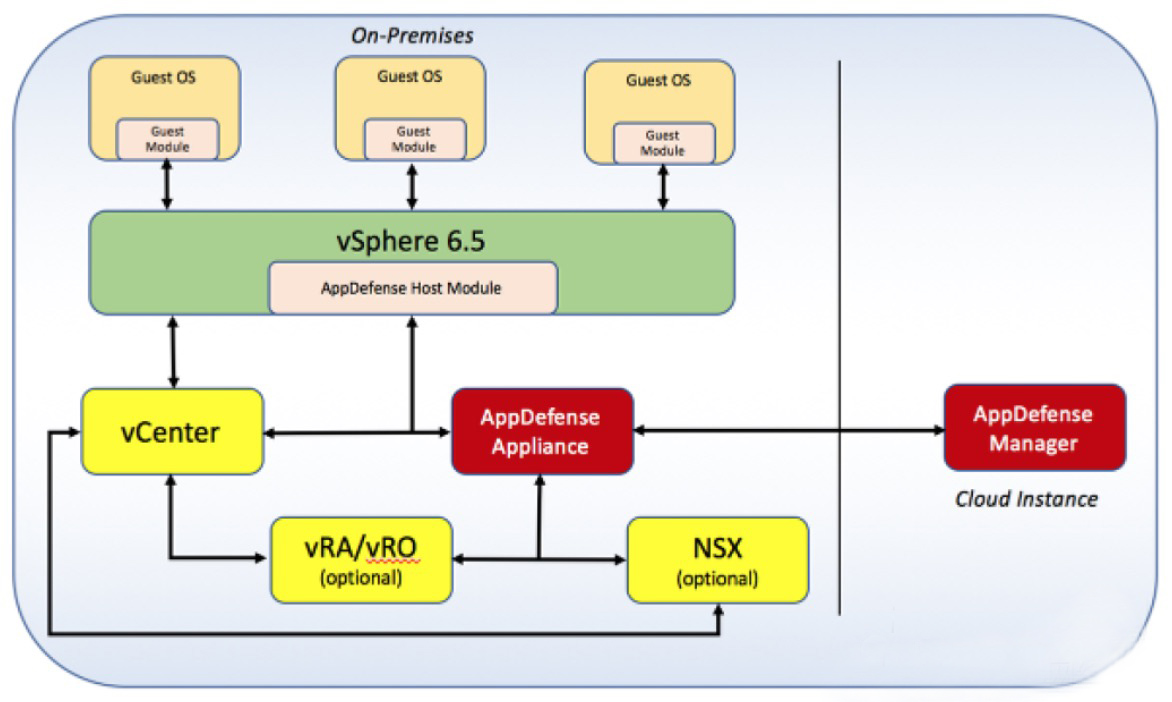
The yellow components in the figure are the traditional modules in the vSphere cluster. vCenter is responsible for managing all the hosts and virtual machines in the cluster. AppDefense obtains this information about the cluster through vCenter and is used to plan the protection scheme for the cluster.
vRA (vRealize Automation) and vRO (vRealizeOchestrator) contain blueprints for automatic application provisioning. AppDefense uses this information to better understand application behavior.
AppDefense also implements some automatic response actions by calling the functions of these components, such as suspending the infected virtual machine through vCenter when a security threat is detected, and isolating a security threat through the virtual firewall function of NSX.
The workflow of AppDefense mainly includes the following steps:
1. Specify the scope of protection (Security Scope): Specify the application to be protected and its related services. These are the monitoring scope of AppDefense.
2. Learn what is a "good" behavior: AppDefense spends one to two weeks to learn the behavior of the protected application under normal conditions. During this time, the status of the protected application is "learning mode"; the end of the study After that, the status changes to "protected mode", indicating that it is protected by AppDefense.
3. Define automatic response rules: AppDefense can detect whether the operating system of the virtual machine has been illegally tampered with, network communication requests that should not occur, whether the AppDefense module itself has been tampered with and other behavioral deviations, and can define automatic response rules for various behavioral deviations.
4. Detect and generate warnings: When a protected application is attacked by malware, because these attacks will not occur during the normal operation of the application, AppDefense can detect these behavior deviations, generate warnings and respond according to predefined rules Automatic processing.
The above is the news sharing from the PASSHOT. I hope it can be inspired you. If you think today' s content is not too bad, you are welcome to share it with other friends. There are more latest Linux dumps, CCNA 200-301 dumps, CCNP Written dumps and CCIE Written dumps waiting for you.
Cisco Dumps Popular Search:
ccna exam what to expect ccnp route exam how many questions ccna practice lab equipment ccna 200-301 david bombal ccnp route 300-101 book download ccnp route dumps 9tut ccna 200-301 official cert guide, volume 2 ccna security pdf ccna question and answer ccna details
Copyright © 2026 PASSHOT All rights reserved.






