100% Pass Cisco, PMP, CISA, CISM, AWS Dumps on SALE!
Get Now
01:59:56
X
How does the IPSec protocol ensure network security?
IPSec (Internet Protocol Security) is a set of open network security protocols formulated by IETF (Internet Engineering Task Force).
It is not a single protocol, but a collection of protocols and services that provide security for IP networks. It provides high-quality, interoperable, and cryptographic-based security guarantees for data transmitted on the Internet.
IPSec mainly includes security protocols AH (AuthenticationHeader) and ESP (Encapsulating Security Payload), key management exchange protocol IKE (Internet KeyExchange), and some algorithms for network authentication and encryption.
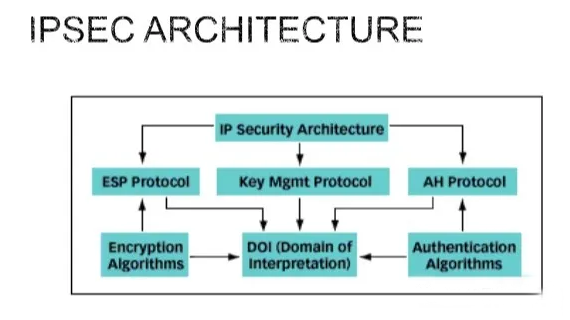
IPSec mainly uses encryption and verification methods. The authentication mechanism enables the data receiver of IP communication to confirm the true identity of the data sender and whether the data has been tampered with during transmission. The encryption mechanism guarantees the confidentiality of the data by encrypting the data to prevent the data from being eavesdropped during transmission. To provide security services for IP data packets.
The AH protocol provides data source authentication, data integrity verification and anti-message replay functions. It can protect communications from tampering, but it cannot prevent eavesdropping. It is suitable for transmitting non-confidential data. The working principle of AH is to add an identity authentication message header to each data packet, which is inserted behind the standard IP header to provide integrity protection for the data.
The ESP protocol provides encryption, data source authentication, data integrity verification and anti-message replay functions. The working principle of ESP is to add an ESP header to the standard IP header of each data packet, and to append an ESP tail to the data packet. Common encryption algorithms are DES, 3DES, AES, etc.
In actual network communication, you can use these two protocols at the same time or choose to use one of them according to actual security requirements. Both AH and ESP can provide authentication services, but the authentication services provided by AH are stronger than those provided by ESP.
basic concepts:
1. Security alliance: IPsec provides secure communication between two endpoints, which are called IPsec peers. It is the foundation of IPsec and the essence of IPsec.
2. Encapsulation mode: IPsec has two working modes, one is tunnel mode and the other is transmission mode. The tunnel mode is used in the communication between two security gateways, and the transmission mode is used in the communication between two hosts.
3. Authentication algorithm and encryption algorithm: The realization of authentication algorithm is mainly through the hash function. The hash function is an algorithm that can accept an arbitrarily long message input and produce a fixed-length output. The output is called a message digest. The encryption algorithm is mainly realized through a symmetric key system, which uses the same key to encrypt and decrypt data.
4. Negotiation mode: There are two negotiation modes for SA establishment, one is manual mode, and the other is IKE auto-negotiation mode.
The working principle of IPSec is similar to that of a packet filtering firewall, and can be seen as an extension of the packet filtering firewall.
When a matching rule is found, the packet filtering firewall will process the received IP data packet according to the method established by the rule.
IPSec determines the processing of received IP data packets by querying the SPD (Security Policy Database). However, IPSec is different from packet filtering firewalls. In addition to discarding and direct forwarding (bypassing IPSec), there is another method for processing IP packets, that is, IPSec processing.
IPSec processing means encrypting and authenticating IP data packets. Only after the IP data packets are encrypted and authenticated, can the confidentiality, authenticity, and integrity of the data packets transmitted on the external network be guaranteed, and secure communication via the Internet becomes possible. IPSec can either only encrypt IP data packets, or only authenticate, or it can be implemented at the same time.
IPSec provides the following security services:
①Data encryption: The IPsec sender encrypts the packet before transmitting it through the network.
②Data integrity: The IPsec receiver authenticates the packet sent by the sender to ensure that the data has not been tampered with during transmission.
③Data source authentication: IPsec at the receiving end can authenticate whether the sending end of the IPsec message is legal.
④ Anti-replay: The IPsec receiver can detect and refuse to receive outdated or duplicate messages.
The way that IPsec protects IPv6 routing protocol messages is different from the current interface-based IPsec process. It is service-based IPsec, that is, IPsec protects all messages of a certain service. In this mode, all IPv6 routing protocol packets generated by the device that require IPsec protection must be encapsulated, and the IPv6 routing protocol packets received by the device that are not protected by IPsec and that have failed to decapsulate are discarded.
Since the key exchange mechanism of IPsec is only suitable for communication protection between two points, in the case of one-to-many broadcast networks, IPsec cannot realize automatic key exchange, so manual key configuration must be used.
Similarly, due to the one-to-many nature of the broadcast network, each device is required to use the same SA parameters (same SPI and key) for the received and sent messages. Therefore, only SAs generated by manual security policies are supported to protect IPv6 routing protocol packets.
The above is the news sharing from the PASSHOT. I hope it can be inspired you. If you think today' s content is not too bad, you are welcome to share it with other friends. There are more latest Linux dumps, CCNA 200-301 dumps, CCNP Written dumps and CCIE Written dumps waiting for you.
Cisco Dumps Popular Search:
ccna data center book ccnp route exam topics pdf ccna test cost ccie certcollection spoto which cisco certification is best ccnp tshoot lab configuration files ccna q and answer cisco ccna online exam free ccna routing and switching practice questions cisco ccna 200-301 content
Copyright © 2026 PASSHOT All rights reserved.






