100% Pass Cisco, PMP, CISA, CISM, AWS Dumps on SALE!
Get Now
01:59:56
X
Three basic components of AAA certification
Three basic components of network security technology AAA certification that you do not know
AAA is short for Authentication, Authorization and Accounting. It is a security management mechanism for access control in network security. It provides three security services: authentication, authorization, and accounting.
An architecture that provides security devices to authorize users to access devices or nearby networks. The authorization feature is used to limit the user's authority after the user is authenticated. Statistics are used to maintain a log of device activity and behavior in the network or network devices.
AAA can perform its functions on the basis of a single user or a single service. In other words, it can be used to authenticate and authorize a single user or service. AAA is set on a router or PIX or any other such device. These devices require AAA to restrict users who access the device itself or the network connected to the device.
The router can use the local database to obtain data for AAA, such as the user name or password or each user's access control list; it can also request an authentication server through protocols such as RADIUS or TACACS+.
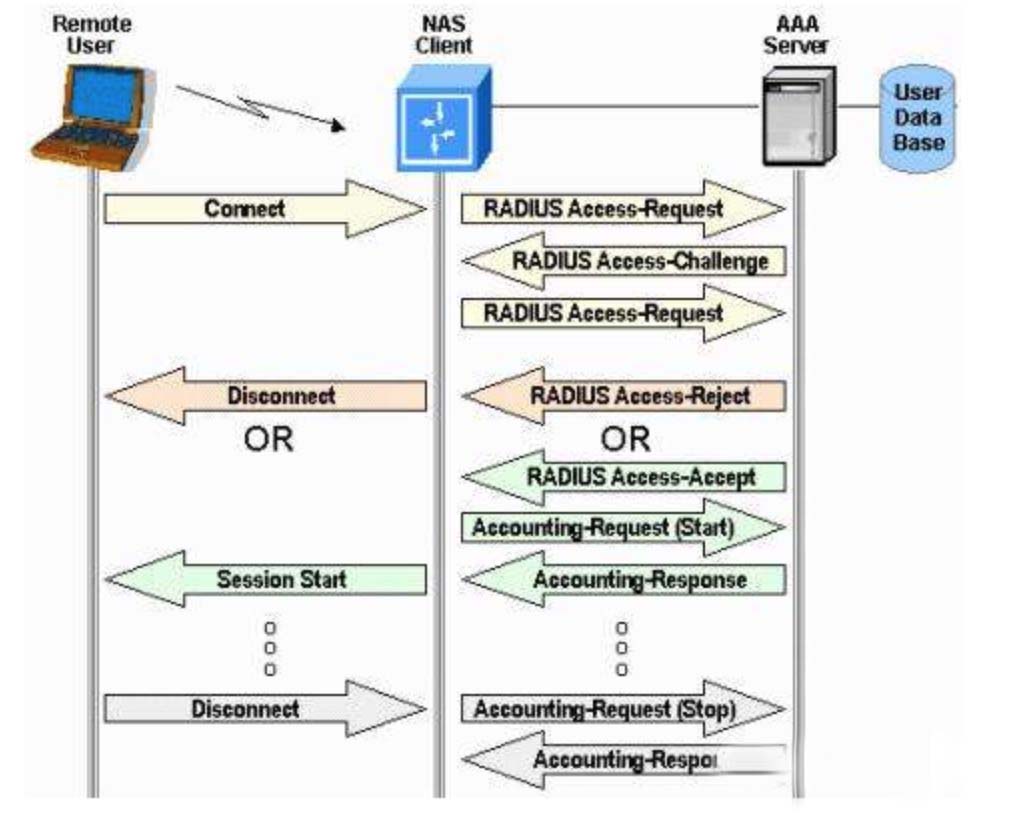
The three basic components of AAA
Authentication: It is to verify the identity of the user and determine whether it is a legitimate user. To put it simply, to judge who you are? What do you have? What is your username and password? Authentication usually adopts the user to input the user name and password to conduct the authority review. The AAA server checks the user's standards with each user in the database.
Authorization: It is to authorize users who are authorized to use which services they can use. Authorization clarifies how much authority an authenticated user can have, what he can do, and what data and information he can access. The authorization process is a combination of a series of coercive strategies, including: determining the type or quality of activities, resources, or what services are allowed by the user.
Accounting: records the resources of users using network services, and this information will be used as the basis for accounting. The audit is a good record of who is on the network, who is doing what, and when. The audit process can be performed based on statistical logs, user information, authorization control, billing, trend analysis, resource utilization, and capacity planning activities of the connection process.
The above is the news sharing from the PASSHOT. I hope it can be inspired you. If you think today' s content is not too bad, you are welcome to share it with other friends. There are more latest Linux dumps, CCNA 200-301 dumps, CCNP Written dumps and CCIE Written dumps waiting for you.
Cisco Dumps Popular Search:
ccie security vs ccie r&s ccna2 ccna book 2019 pdf ccna 200-125 latest dumps 2017 cisco ccnp switch book ccna 1 practice final exam 2020 cisco spcor 350-501 book ccna keith barker ccie lab blueprint 5.1 ccna 200-301 pdf download
Copyright © 2026 PASSHOT All rights reserved.






