100% Pass Cisco, PMP, CISA, CISM, AWS Dumps on SALE!
Get Now
01:59:56
X
How to prevent IPv6 VPN breakthrough?
Today I will tell you how to prevent IPv6 VPN breakthroughs.
Without a properly configured remote access VPN, IPv6 traffic from remote devices may escape corporate security controls.
This vulnerability occurs because some of these remote access VPNs are configured to inspect and apply security controls only to IPv4 traffic as it passes through the VPN concentrator, without enabling similar protection for IPv6 traffic.
This allows IPv6 traffic to access the Internet directly without the need to apply these controls. This problem is known as the IPv6 VPN breakthrough and is well known, but often overlooked.
Why Ignore IPv6 VPN Breakthrough
Many businesses don't know how often IPv6 is used on devices that access their network through a VPN. Phones, tablets and laptops used to remotely access corporate networks typically support IPv6, and broadband and cellular services may also support IPv6 for Internet access.
As a result, companies generally do not consider IPv6 as a security factor. They configured their VPN to inspect only IPv4 traffic, which allowed mobile devices to freely access IPv6 sites, which could pose a danger to business networks, devices, and data.
The way IPv4 protection works is that once a VPN is established, the VPN concentrator checks the traffic bound to the Internet and blocks the traffic bound to the destination determined by the policies configured by the enterprise.
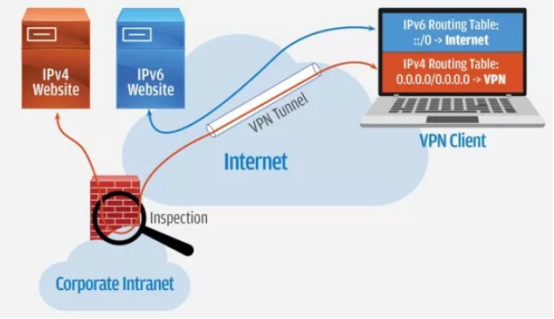
The figure above shows a typical corporate VPN user laptop with an IPv4 VPN tunnel established only back to the perimeter of the corporate Internet. The red line indicates IPv4 traffic that is targeted by the enterprise to apply traffic inspection and security controls to Internet-bound traffic. All IPv4 traffic must pass through the VPN tunnel and cannot directly access the Internet, but IPv6 traffic indicated by the blue line is OK.
Most corporate VPNs enforce so-called non-split tunnels to enforce security by forcing all IPv4 connections to traverse the VPN. Without a split tunnel, once a VPN connection is established, the remote device cannot establish a separate connection to the entire Internet.
Usually, this is done by advertising the IPv4 default route (0.0.0.0/0.0.0.0) to the VPN client over the VPN tunnel. The IPv4 default route is inserted into the routing table of the VPN client and is represented by a red field on the laptop screen in Figure 1. Therefore, when end users run a VPN, all their connection attempts to IPv4 websites are checked through the company's intranet hairpin.
The security problem is that companies usually do not apply the no split-tunneling setting on the VPN to include the IPv6 default route, which is also in the VPN client routing table (:: / 0), which is indicated by the blue field in the figure. Laptop screen. This allows IPv6 traffic to access the Internet directly, bypassing any company's Internet perimeter security measures.
Enterprises should face the fact that they already have IPv6-enabled devices on their networks and mobile employees, so they should take a proactive approach to eliminate this security breach.
How to prevent IPv6 VPN breakthrough
The recommended way to produce the best results is to control the situation by enabling IPv6 across the VPN and the company. Businesses should start enabling IPv6 connections around their Internet perimeter and then establish IPv6 connections with VPNs. Modern enterprise perimeter firewalls and their VPN software are already capable of using IPv6, just enable and configure it. In this case, the traffic looks like the figure below.
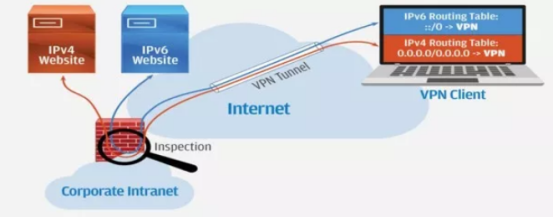
This is the recommended IPv6-enabled VPN architecture, where VPN clients use both IPv4 and IPv6 network connections. It has both IPv4 and IPv6 routing tables, and each of their default routes directs Internet traffic to the VPN tunnel.
This allows the company's Internet peripheral systems to check both protocols and apply security protections equally, preventing IPv6 VPN breakthroughs.
The second option is to use a VPN client, which prevents IPv6 leaks on its own. For example, Cisco AnyConnect clients paired with Cisco's ASA security appliance can control how split tunneling is configured on IPv6-enabled clients.
Similarly, Palo Alto Networks GlobalProtect VPN and Fortinet SSL VPN FortiClient also support IPv6. Just enable IPv6 and control it through a VPN policy.
Unfortunately, the approach taken by some organizations is to break IPv6 connections while establishing a VPN tunnel. In this case, the VPN server advertises the IPv6 default route (:: / 0) to the routing table of the VPN client to direct all IPv6 connections through the VPN tunnel.
However, when the VPN and the company's internal network use only IPv4, all IPv6 connections will be dropped. If an enterprise does not have an IPv6 connection to the VPN, the enterprise should not advertise this IPv6 default route, as this will cause application connectivity issues for all VPN clients that try to access applications using IPv6.
Users who need to access an IPv6-enabled site will initially experience a failed connection and then be delayed due to client fallback to IPv4.
The third option is to register the Domain Name System (DNS) to prevent IPv6 VPN breakthroughs. In this case, VPNs that only retain IPv4 will remain in place, but all DNS address resolution will be forced along the tunnel. IPv6 DNS queries will be suppressed, but IPv4 queries will succeed.
By making certain IPv6-enabled applications perform poorly in IPv6 DNS resolution and connection attempt timeouts, and fallback to IPv4, this can have an adverse effect. This also makes troubleshooting application issues more difficult as IT administrators need to find applications that may be using IPv4 and / or IPv6 and try to separate the issue from DNS, connectivity, VPN policies and VPN client configuration.
The longer an enterprise waits to build an IPv6-enabled enterprise remote access VPN, the more serious the problem of IPv6 VPN breakthroughs. End-user devices will increasingly use IPv6, and less and less IPv4 traffic will be returned through corporate VPNs. Businesses should be aware of the breakthrough issues of IPv6 VPNs and work hard to take steps to enable IPv6 on their Internet borders and remote access VPNs.
The above is the news sharing from the PASSHOT. I hope it can be inspired you. If you think today' s content is not too bad, you are welcome to share it with other friends. There are more latest CCNA 200-301 dumps and CCIE Written dumps waiting for you.
Cisco Dumps Popular Search:
ccie security 4.1 cisco 200 301 study material cisco ccna classes cost for ccna security exam how to master ccnp route rene molenaar cisco certification in cyber security ccnp route tutorial ccna 1 v7.0 final exam answers full ccna exam in nepal 400-251 ccie security exam cost
Copyright © 2026 PASSHOT All rights reserved.






